HUMAN’s Satori Threat Intelligence Team says that a scheme called Merry-Go-Round, at its peak, reached 782 million bid requests a day.
HUMAN’s Satori Threat Intelligence issued a Security Threat Alert this morning, detailing a scheme it calls Merry-Go-Round. At its peak, Merry-Go-Round reached 782 million fraudulent bid requests daily, cleverly evading detection through a sophisticated cloaking mechanism.
Although the scheme has been detected and interrupted, the Satori team warns that the industry isn’t out of the woods as the operation is still active and accounts for 200 fake million bid requests daily.
How it Works
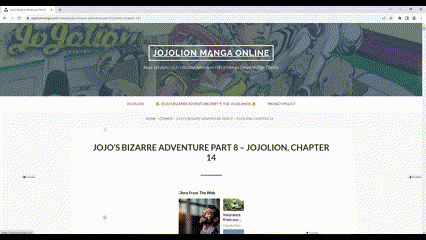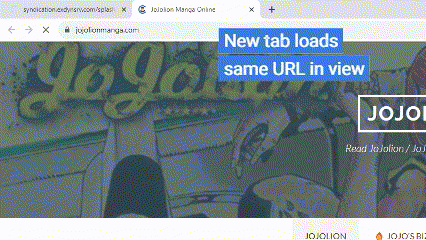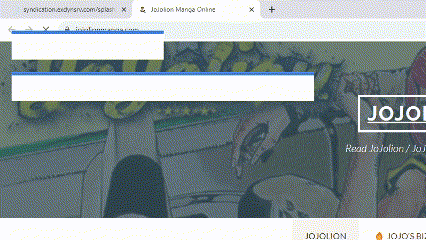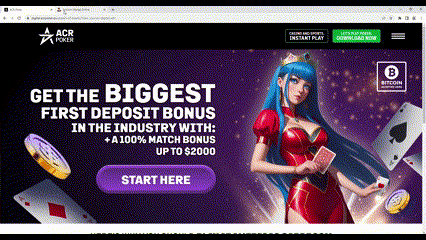
Consumers visit several piracy and adult-content websites that are affected by Merry-Go-Round (HUMAN has not published the names of those domains).
The Merry-Go-Round kicks off when a user clicks on a story or video from one of the affected site’s directory. An overlay hijacks the click, opening a second tab to display the content the user expects to see. Meanwhile, the original tab- now out of the user’s focus- redirects the user to a series of pages on fake sites that the fraudsters created for the scam. Those sites, all of which have benign names such as beautyparade.co and caloriamania.co don’t have any actual content. They’re simply pages cluttered with ads that sell via the open markets.
The volume of impressions created on these out-of-focus tabs is immense. Let’s say a user visits one of the affected sites to download a movie and doesn’t notice the out-of-focus pop-under tab for the entire two hours he or she watches the movie. Every 60 seconds, the out-of-focus tab directs the user to the next page in the fake domains that make up the Merry-Go-Round network. Each page can contain up to 100 fake ads, so over the course of that movie, some 12,000 bid requests will occur. If, like many people, the user doesn’t notice the open tab and leaves it open for 24 hours, some 150,000 ad requests will be generated.
The more tabs left open, the more fake bid requests sent to SSPs. In one instance, HUMAN saw more than 789,000 ad requests associated with Merry-Go-Round from a single residential IP address in a single day.
Cloaking Mechanism
So, how do brands and their advertising partners not know these sites are fake? Don’t they audit sites in their networks?
To evade detection, the Merry-Go-Round perpetrators have deployed a sophisticated domain cloaking mechanism built on path-dependent domain loading, a method in which the content displayed on the website depends on how the user arrives there. Brand auditors who directly type a Merry-Go-Round domain into their browsers will see a seemingly legitimate, if mundane, website, as they have programmed those sites to prevent redirects during direct visits.
“These actors have gone out of their way to conceal what they’re doing,” explained Will Herbig, Director of Fraud Operations at HUMAN Security. “They scrubbed all the referral information between the Merry-Go-Round domains and the piracy domains, as well as all the referrals within the Merry-Go-Round network. They’ve also added some anti-crawler features to the website. As a result, it is very challenging for a layperson at a brand to detect the scheme.”
To protect their budgets from the Merry-Go-Round scheme, Herbig recommends that brands know as much about their partners as possible. Direct relationships can help brands avoid these types of situations.
The rise of domain cloaking techniques like path-dependent domain loading and IP address filtering presents a significant challenge in ad fraud detection. These techniques allow fraudsters to mask a website’s true nature, creating a major disconnect between what advertisers believe they’re buying (ad impressions on legitimate sites) and what they actually get (impressions on hidden, malicious content).
“We found quite a bit of fraud around this domain cloaking, and we’re going to be publishing other things along those lines and throughout the rest of the summer, but it continues to be an area where we’re seeing quite a lot of fraud, and the techniques there are evolving and making it you know, harder and harder for people, especially advertisers to know whether or not what they’re getting is actually real or not,” Herbig said.
For more details, including examples of the iFrames and overlays used in the Merry-Go-Round scheme, download the report, Satori Threat Intelligence Alert: Merry-Go-Round Conceals Ads from Users and Brands.