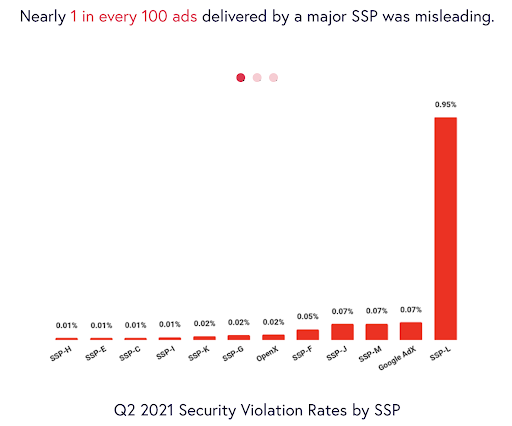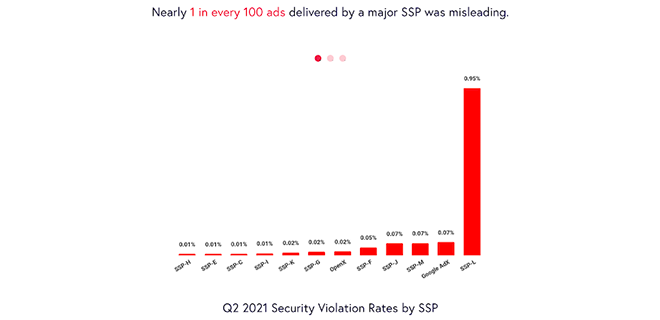
In Q1, Confiant tracked impressions from over 100 SSPs. However, more than 75% of global impressions originated from just 12 providers commonly used by publishers.
I caught up with John Murphy, Chief Strategy Officer at Confiant about some surprising findings in Confiant’s Malvertising & Ad Quality Index Q1 2021 report. It seems Google has slipped in the SSP rankings related to malvertising and ad quality.
A perennial strong performer, Google experienced an uncharacteristic setback this quarter. Their security violation rate increased from 0.05% in Q4 to 0.18% in Q1 and exceeded the industry average for the first time. SSP-L had the highest Security violation rate, coming in at 213x the rate of the best performing SSP. SSP-L was also the worst performer in Q4.
John explains:
Rob Beeler: Considering Google’s size in the marketplace, what impact might this have on users and the amount of malicious activity that’s actually getting to users and not getting filtered out?
John Murphy: It’s huge. If Google sneezes, everybody else catches a cold. That’s how large they are compared to the rest of the industry. So, I think largely over the next few quarters, whether the industry runs clean or not is largely going to be dependent on how Google addresses this issue.
Rob Beeler: How much does the ranking of the SSPs in your report vary from quarter to quarter?
John Murphy: There’s a fair amount of variance. We definitely have seen instances where an SSP will perform very well one quarter, and then very poorly the next quarter, and even swing back the quarter after that. So there are some SSPs where we do see that high level of variance, and it really comes down to whether they were targeted with an attack. Besides Google, there is a group of SSPs that consistently performs well, and very rarely runs into issues with malvertising.
Rob Beeler: What do security companies need to do to protect users from these new threats?
John Murphy: Some of our competencies from previous versions of malvertising are still very much relevant. In these new attacks, cloaking isn’t always utilized, but in a lot of them, they do cloak. A malvertiser may submit what appears to be a completely innocuous creative for review by a DSP, or an SSP, just to get it into the ecosystem. But then that creative will change once the campaign is live, and perhaps only to certain segments of users. So that can be challenging to detect, because obviously, in that case, the threat actor is actively trying to evade any sort of detection, any of the quality control mechanisms that are put in place by the industry.
Companies like Confiant have become very good at detecting cloaking because we have instrumentation on the client-side. So in real users’ browsers, we’re going to see any payload that is being delivered, any change in the nature of the advertisement between when it might’ve originally entered the ecosystem to five minutes ago.
That’s still relevant. What has changed is there’s now a need to not only look for those technical markers of a threat but also the business markers. It requires being able to do that research on the entities that are behind an ad and the business models behind different ads, because you need to look not only, again, for maybe signs of cloaking, but also for language or offers that are frequently used to swindle users out of their money. Some are fairly straightforward, any sort of Bitcoin investment opportunity probably requires a close look, but this certainly extends to other sorts of offers in categories where you wouldn’t necessarily think there was a high probability that it was a scam.
Download the Malvertising & Ad Quality Index Q1 2021 report to learn more about the state of creative quality in digital advertising based on 156 billion impressions monitored in real-time in Q2 2021.